CloudFirewall is a simple, SDN based firewall, which can be used in order to forward or block certain types of traffic between two different networks. It supports three different work modes: black-list based blocking, white-list based forwarding, and a pass-through mode which forwards all traffic, but still gathers different statistics on it.
It also features a simple web based UI which can be used to manage settings and inspect statistics on the network traffic and the firewall’s functionality.
CloudFirewall is implemented as an SDN controller, which is programmed to forward or block certain TCP/UDP flows, where a TCP/UDP flow can be uniquely identified by the five-tuple of < source IP, destination IP, transport protocol type, source port, destination port >.
This SDN controller controls, using the OpenFlow protocol, an underlying SDN switch which interconnects two different networks.
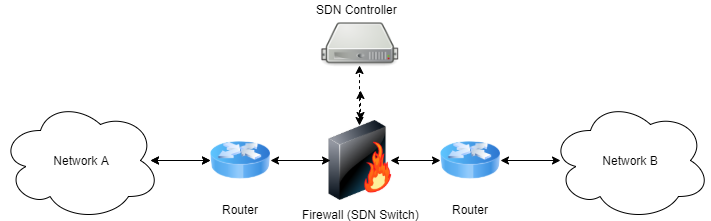
Whenever a packet starting a new flow is received at this switch, it forwards it to the controller, which in turn decides whether this flow should be forwarded to the other network or otherwise blocked altogether. This decision based upon the firewall’s current work mode (white-list / black-list / pass-through) and its current defined rules set. When such decision is made by the controller, it installs an appropriate forwarding rule in the switch so that future packets belonging to the same flow will be handled in the same manner.
The implementation consists of two different parts:
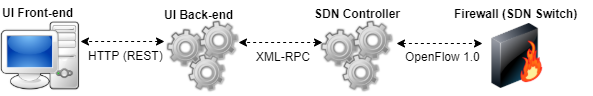
As explained above, the firewall is implemented as an SDN controller.
It is written in Python and is built above the POX framework. It exposes an XML-RPC based API which allows manipulating the firewall’s behavior (i.e: changing the firewall’s work mode, adding and removing forwarding rules). See this API file for a complete functions list.
You can find the firewall’s source code under the sdn-fw folder.
The firewall’s UI is implemented as a web application. It’s back-end is written in Python above the Flask micro-framework. It exposes a RESTful API which allows manipulating the firewall’s settings, i.e: changing it’s current work mode, adding or removing forwarding rules, etc.
It also allows querying for certain statistical and event based information regarding the traffic passed through the firewall (i.e: detailed information on flows that were recently blocked by the firewall).
You can experiment with the RESTful API by invoking the api_tester.py script.
The front-end is simplemented as a single page application, and is written in HTML/CSS/JS.
For rendering the visual charts, we used the charts.js library.
You can find the code unser the cloudfirewall folder.
The easiest way to experiment with CloudFirewall is to set it up on a Mininet network. We provided a simple Mininet network topology file that you use to easily create a network that consists of two LANs, interconnected by CloudFirewall.
In order to setup this network follow the next steps:
-
Install Mininet v2.1.0 64bit on your target machine using the instructions found here.
Alternatively, simply grab the preinstalled Mininet 2.1.0 64 bit VM (make sure you get the right version).
-
Install POX on your target machine by following the instructions found here.
Note: the Mininet VM comes with POX preinstalled, so skip this step if you chose to use this VM.
-
Make sure POX is on the dart branch by entering the POX folder (/home/mininet/pox in the Mininet preinstalled VM) and running:
-
Clone CloudFirewall’s git repository by running:
git clone https://github.com/matanby/CloudFirewall.git
-
Install Python development tools and PIP by running:
apt-get install -y python-dev python-pip
-
Install all package dependencies by running:
sudo pip install -r CloudFirewall/requirements.txt
-
Run the SDN firewall:
cd CloudFirewall/sdn-fw/
chmod +x ./run_fw.sh
./run_fw.sh
Note: the run_pox.py script is configured to run POX from /home/mininet/pox, if you have POX installed in some other path, edit this file and change it accordingly.
8. Run Mininet with the sample network topology provided:
cd CloudFirewall/sdn-fw/test/
chmod +x ./run_mininet.sh
./run_mininet.sh
-
Run the UI web application:
cd CloudFirewall/cloudfirewall/
python app.py
-
Access the UI by entering: http://[MININET_HOST_IP]:5000
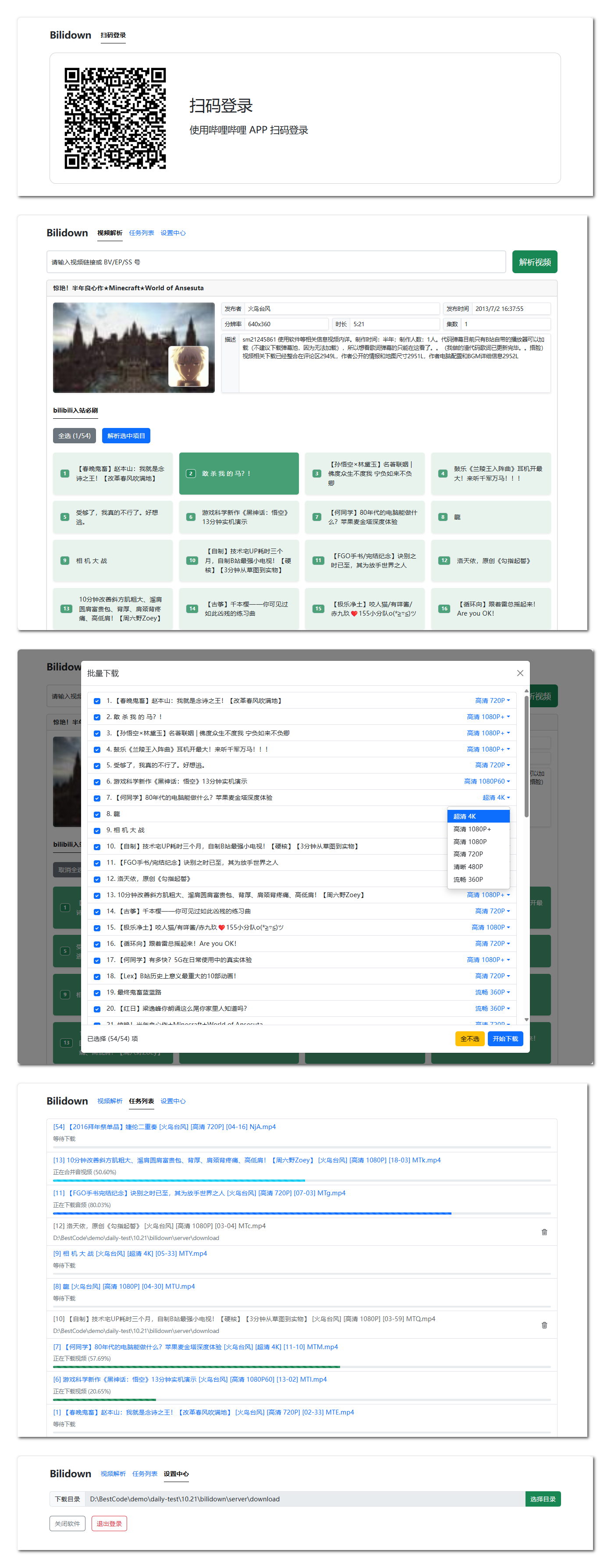
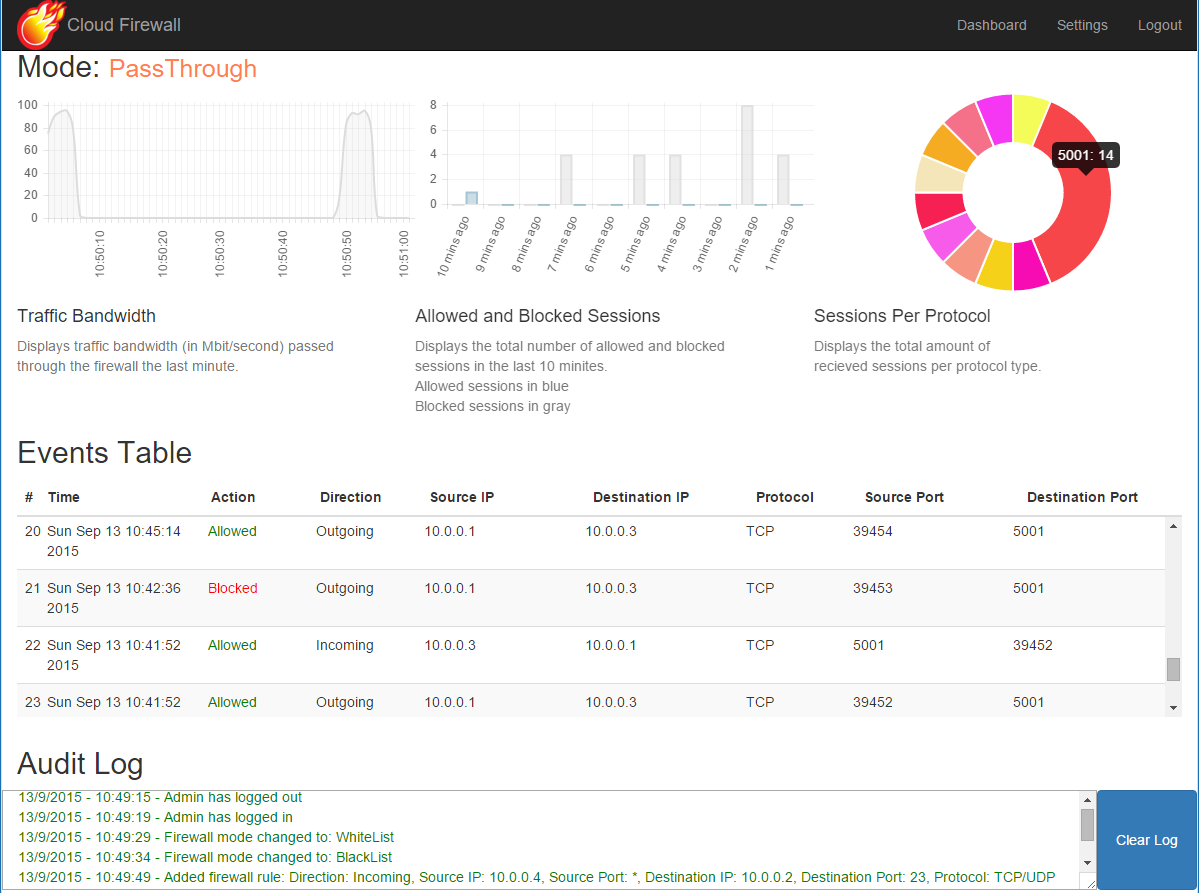
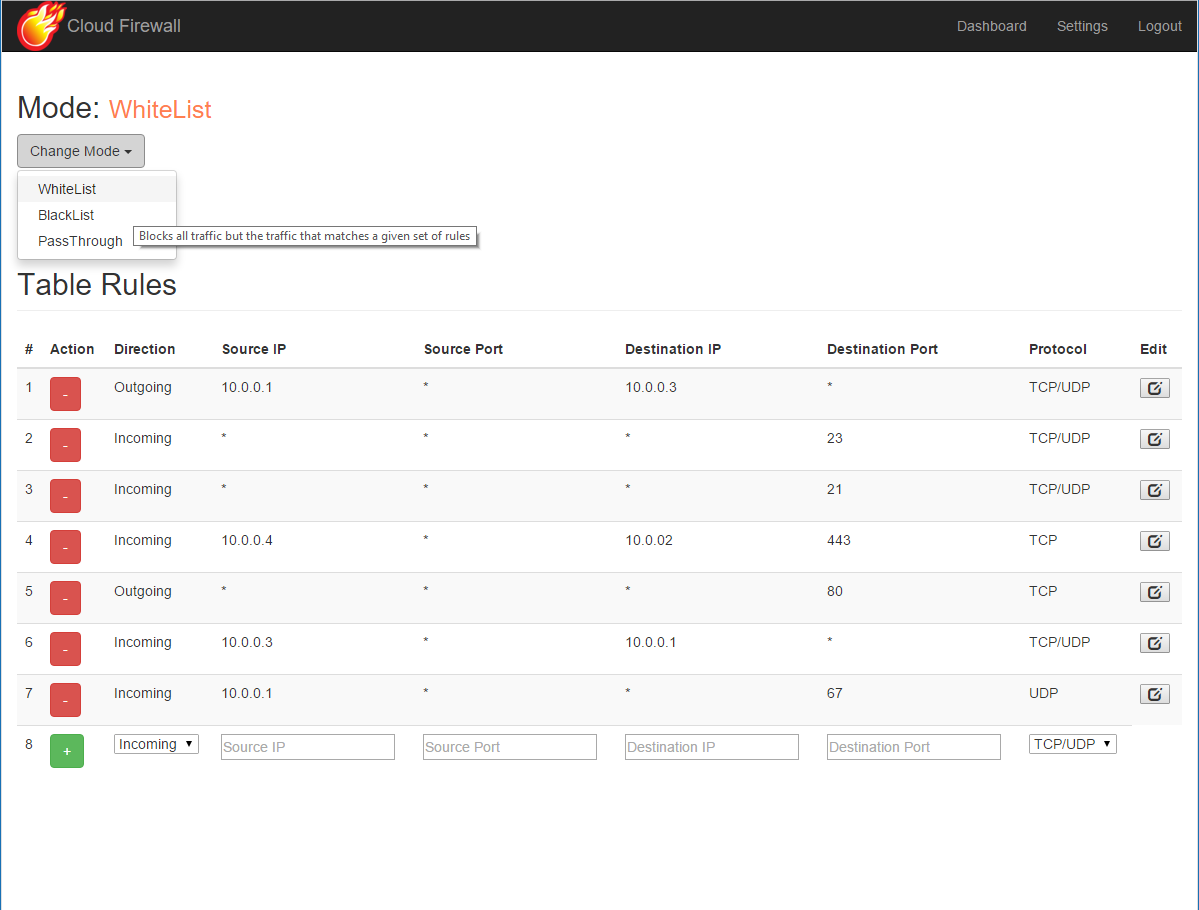
Here are a couple of screenshots of the web UI:
The dashboard:
The settings section:
This project was created by Matan Ben-Yosef and Nir Parisian as a part of the course Advanced Operating Systems & Cloud Technologies (67788), instructed by Dr. Yaron Weinsberg and Prof. Danny Dolev, in spring semester of 2015, Hebrew University Of Jerusalem.